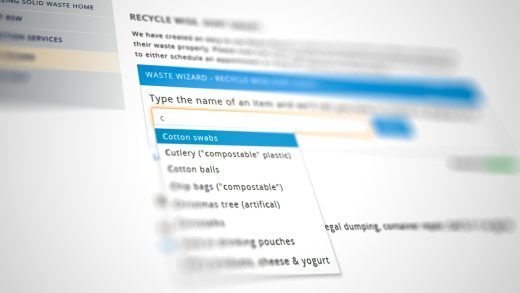
City Launches Waste Wizard to Help Residents Recycle Wise and Sort Smart
The City of Sacramento – Recycling and Solid Waste Division, has launched the Waste Wizard. This new web-based application will answer resident’s questions on how best to recycle or dispose of waste using City services or other local facilities. The launch coincides with national America Recycles Day, which is November 15, 2015.







Recent Comments